Cryptocurrencies, secured by cryptography and operating on blockchain technology, are transforming the commerce payment landscape worldwide. Today, the amount of people holding and exchanging crypto tokens exceeds 420 million, according to the Triple-A study, which indicates digital currency payments are becoming more mainstream, with crypto payment systems also on the rise.
Despite their many benefits, the blockchain’s inherent transparency poses unique challenges, as the immutable recording of transactions could inadvertently disclose more information than users might anticipate.
To manage risks effectively, adopting the best crypto payment security practices is a priority for businesses wanting to deliver a safe and reliable payment experience to their customers. In this article, we will explore the best practices businesses should follow to uphold privacy in the dynamic landscape of cryptocurrency transactions.
Key takeaways
- Cryptocurrencies offer pseudonymity, but they are not completely anonymous due to public transaction records.
- Strict data protection measures and compliance with regulations are necessary for businesses involved in cryptocurrency transactions.
- To maintain customer privacy, businesses should adopt secure crypto payment gateways, implement a multi-faceted approach to privacy protection, and follow best practices for security.
Cryptocurrency and Privacy Concerns
In the midst of today’s digital landscape, where everything is interconnected and data privacy is a major concern, cryptocurrencies offer alternative solutions to traditional monetary systems. Individuals are increasingly turning to cryptocurrencies like Bitcoin, which enable transactions without revealing personal details.
Anonymity vs Transparency
Cryptocurrencies operate on blockchain technology, which allows for peer-to-peer transactions without revealing personal details. This has been a significant factor in the rise of Bitcoin as a preferred monetary network. However, while cryptocurrencies offer pseudonymity, they are not entirely anonymous.
Transactions on the blockchain are recorded publicly, making them visible to anyone with access to the network. Once an address is linked to an identity, transactions can be traced back to that individual.
To address privacy concerns in crypto, coins like Monero and Zcash implemented advanced cryptographic techniques to obscure transactions. However, the increased use of these privacy coins has also raised regulatory concerns over their potential for illicit activities.
Data Protection and Regulations
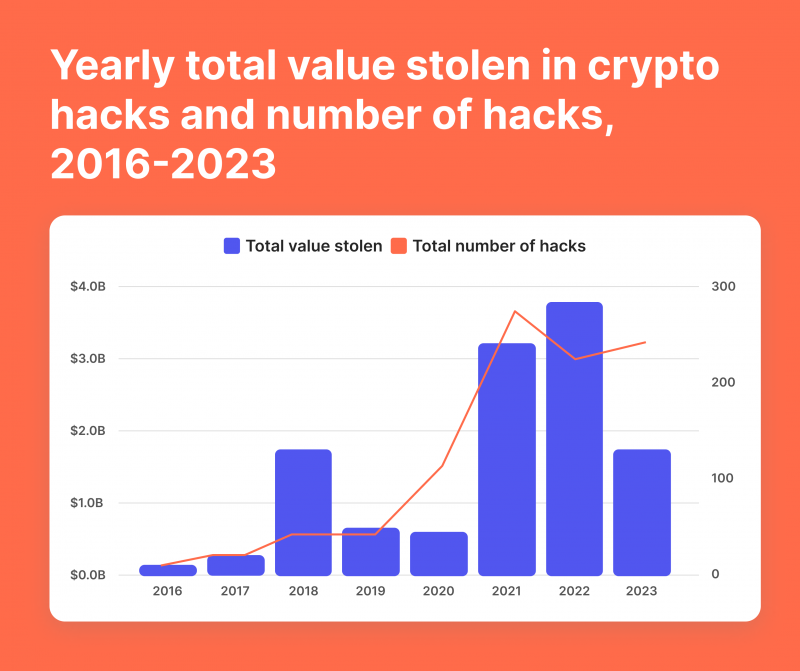
Breaches at cryptocurrency exchanges and crypto payment systems have also highlighted the need for businesses to implement strong security measures. In 2023, even though the volume of funds stolen decreased by 54.3% year-by-year (due to less hacking in DeFi protocols), it still amounted to $1.7 billion, which is an alarming number.
This is why, in the EU, for example, under GDPR (General Data Protection Regulation), businesses that process personal data are required to obtain explicit consent and provide transparent information on how the data will be used.
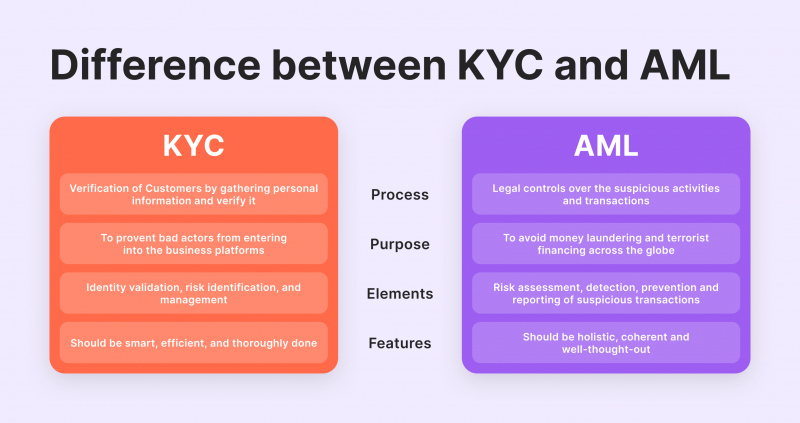
In addition, cryptocurrency exchanges and platforms must comply with anti-money laundering regulations (AML) and Know Your Customer (KYC) guidelines. This means implementing strict identity verification processes, monitoring transactions for suspicious activity, and reporting any suspicious behaviour to authorities.
Adopting Secure Crypto Payment Gateways
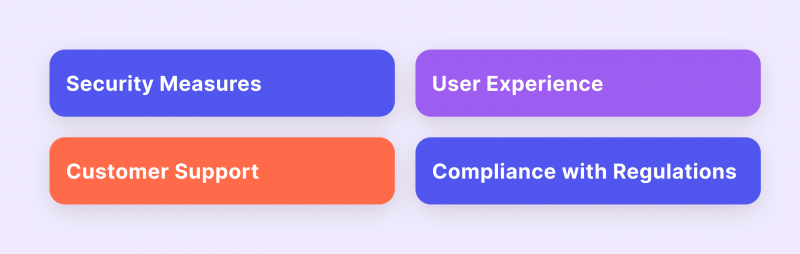
One of the ways to secure sensitive data when using a crypto payment system is by adopting a secure and reliable payment gateway. Focus on several key aspects to ensure smooth, secure transactions that protect both your interests and those of your customers. Here’s a breakdown of the essential factors to consider:
Security Measures
Always opt for gateways with robust security protocols, including two-factor authentication (2FA) and advanced encryption, to protect against unauthorised access and data breaches.
Integration and User Experience
Choose a secure payment processing gateway that offers seamless integration with your existing systems, ensuring a smooth user experience with minimal disruption to your operations.
Look for low-code deployment options for ease of setup, and ensure the gateway provides a user-friendly checkout page that’s mobile-responsive.
Customer Support and Compliance
Ensure reliable customer support is available to address any issues or questions that may arise quickly.
Furthermore, verify that the gateway adheres to stringent KYC and AML procedures to maintain regulatory compliance.
Essential Privacy Protection Measures for Businesses
Businesses must implement multi-faceted strategies to fortify customer privacy within the realm of crypto payments, incorporating proactive protection strategies.
Privacy by Design
One of the fundamental principles for safeguarding user privacy is implementing “privacy by design” in all business processes. This approach entails building privacy into every stage of the product development life cycle rather than adding it as an afterthought. For crypto businesses specifically, this could involve:
- Generate a new address for each transaction to prevent address reuse and enhance anonymity.
- Obtain explicit user consent before processing their data, ensuring compliance with regulations such as GDPR.
- Make privacy features user-friendly and invest in robust cybersecurity measures to protect sensitive user data from cyber threats.
Security Best Practices
How do we minimise the risk of security breaches and ensure the confidentiality and integrity of customer data? Businesses must follow security best practices when using crypto payment systems, such as:
- Conduct regular security audits to identify and mitigate vulnerabilities in their systems.
- Use end-to-end encryption and multi-factor authentication to safeguard sensitive payment data during transactions.
- Maintain up-to-date hardware wallets and software and enable continuous transaction monitoring to detect any suspicious transactions promptly.
Proactive Protection Strategies
Apart from implementing technical measures, businesses must also adopt proactive protection strategies to strengthen their defence mechanisms against potential data breaches. These may include:
- Educate employees on security risks and best practices to prevent unauthorised access or accidental disclosure of sensitive information.
- Develop tailored solutions for individual business needs instead of relying on a one-size-fits-all approach to security.
- Utilise advanced tools and technologies to detect and prevent insider threats and data leaks proactively.
Implementing Robust Data Encryption Techniques
In the realm of crypto payment systems, robust data encryption is fundamental to ensuring transaction protection and customer privacy. Here’s how businesses can implement effective encryption techniques:
Choosing the Right Encryption Type
- Symmetric Encryption: Utilise algorithms like AES, DES, TDES, and Twofish. AES is particularly recommended for its global use in securing files, applications, and communications across various platforms.
- Asymmetric Encryption: Deploy methods such as RSA and ECC. RSA is suitable for encrypting documents and messages on a smaller scale, while ECC provides stronger security with smaller key sizes, which is beneficial for mobile devices.
Implementing Encryption Across Data States:
- Data in Transit: Secure data as it moves across networks using SSL/TLS protocols, which typically incorporate AES encryption.
- Data at Rest: Protect stored data, such as on servers or databases, by encrypting the storage media itself or the individual files.
- End-to-End Encryption: Ensure that data remains encrypted from the sender to the recipient, preventing intermediaries from accessing readable data.
Educating Customers on Data Privacy
You should equip customers with knowledge and best practices for handling their personal information. Here are crucial tips and resources to help users protect their digital assets:
Inform Customers About Privacy Risks
Customers must be aware of the privacy risks associated with cryptocurrency transactions. It’s vital they understand how blockchain transactions are recorded publicly and the ways in which their transaction data could be traced back to their real-world identity.
Offer Practical Protection Tips
Remember, your customers are not experts in cybersecurity or cryptography. Therefore, it’s your responsibility to provide them with practical tips for securing their cryptocurrency transactions. Some tips you can offer:
- Secure your wallet with strong, unique passwords.
- Use hardware wallets to store cryptocurrencies securely.
- Regularly update software to protect against vulnerabilities.
- Enable two-factor or biometric authentication for an additional layer of security.
- Review account activity periodically to spot any unauthorised transactions.
Staying on Top of Regulatory Compliance and Privacy Laws
In the ever-evolving domain of cryptocurrency, businesses must navigate the complex interplay between maintaining customer privacy and adhering to regulatory compliance.
With the rise of digital payments and crypto assets, the regulatory compliance landscape for crypto payment systems is witnessing increased scrutiny. Authorities are actively working on establishing codified rules and frameworks to oversee the operations of stablecoins, Central Bank Digital Currencies (CBDCs), and other digital assets.
Businesses must stay vigilant and responsive to these regulations, which focus on several key areas:
- Data Security and Reliability: Ensuring that the network and services provided are secure and reliable.
- Liquidity and User Experience: Guaranteeing sufficient liquidity for operations and a seamless user experience.
- Dispute Resolution and Consumer Protection: Establishing clear protocols for handling disputes and protecting consumers from fraud.
Companies must also be mindful of how they manage consumer disputes and claims, as regulatory bodies, state attorneys general, and members of Congress are paying close attention to these aspects.
To effectively manage compliance and privacy law adherence, businesses should consider the following steps:
- KYC and AML Compliance: Implement strict Know Your Customer and Anti-Money Laundering measures to prevent illicit data activities.
- Regulatory Awareness and Adaptation: Stay informed about regulatory changes and adapt business practices accordingly to avoid stifling innovation.
- Taxation and Reporting: Cryptocurrency transactions must be reported as gross income based on their fair market value at the time of receipt in the U.S., with each transaction tracked for taxation. The IRS categorises cryptocurrency as “property,” adding another layer of complexity for businesses managing multiple daily transactions.
Businesses should continuously research and comply with local regulations, adapting to changes such as the EU’s MiCA, which aims to increase consumer protections and establish clear industry conduct.
Final Thoughts
As the digital marketplace expands, safeguarding customer privacy in crypto transactions becomes increasingly critical. The adoption of secure crypto payment processing gateways and proactive customer education on privacy are vital steps that businesses must take to ensure a secure and compliant transactional environment.
The dynamic nature of cryptocurrency demands diligence and foresight from businesses to stay abreast of regulatory changes and protect customer data. By integrating these best practices, companies can pave the way for a secure and innovative digital economy.
FAQ
How is privacy maintained on the blockchain?
Privacy on the blockchain is maintained through the use of encryption, pseudonymity, and selective disclosure. Public blockchains utilise pseudonymous transactions to balance privacy with the transparency needed to maintain public trust. Private blockchains may offer additional privacy features.
How does Bitcoin offer more privacy than traditional financial systems?
Bitcoin’s protocol enhances user privacy by not necessitating the disclosure of personal information, such as names or addresses, for transactions. This reduces the ease with which third parties can track users’ financial activities, offering more privacy than traditional banking systems.
What factors influence consumer trust in crypto payments?
Studies show that consumer trust in crypto payments is significantly influenced by their perceptions of information privacy risk, perceived anonymity, and the traceability of transactions.
What are the potential drawbacks of using cryptocurrencies for payments?
Some disadvantages of using cryptocurrencies as a payment method include the lack of legal protections that are available with credit and debit card transactions, the typically irreversible nature of cryptocurrency payments, and the fact that some transaction details may become public.